Arp-Spoofing | Check spelling or type a new query. We did not find results for: Maybe you would like to learn more about one of these? Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network.
Maybe you would like to learn more about one of these? Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. We did not find results for: Check spelling or type a new query. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network.
We did not find results for: Maybe you would like to learn more about one of these? In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network. Check spelling or type a new query. Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta.
Maybe you would like to learn more about one of these? We did not find results for: In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network. Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. Check spelling or type a new query.

Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. We did not find results for: In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network. Maybe you would like to learn more about one of these? Check spelling or type a new query.
We did not find results for: In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network. Maybe you would like to learn more about one of these? Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. Check spelling or type a new query.
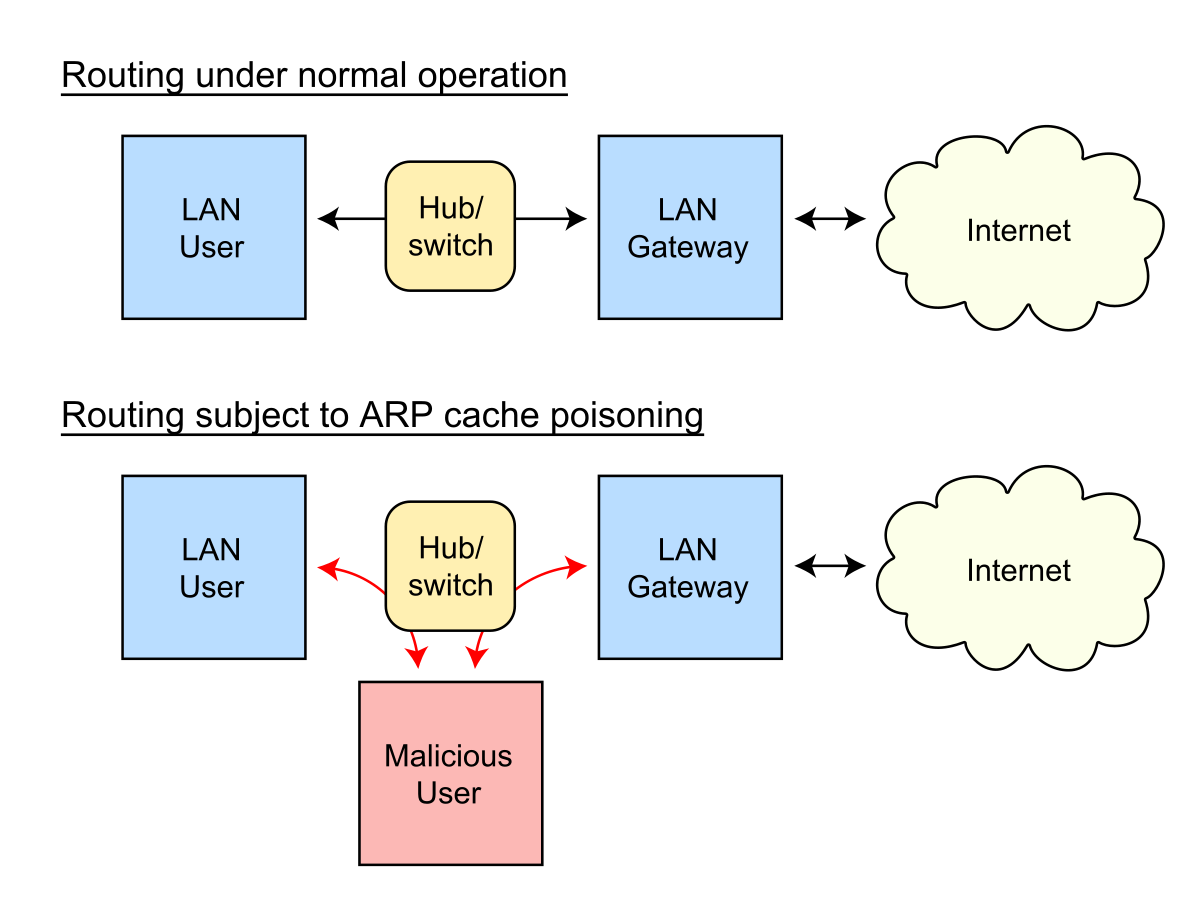
We did not find results for: In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp) messages onto a local area network. Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta. Check spelling or type a new query. Maybe you would like to learn more about one of these?
Arp-Spoofing: Generally, the aim is to associate the attacker's mac address with the ip address of another host, such as the default gateway, causing any traffic meant for that ip address to be sent to the atta.
0 Tanggapan